As cyber threats continue to evolve in sophistication, businesses need robust solutions to defend their digital infrastructure. CrowdStrike has emerged as a leader in endpoint security, providing next-generation protection against various types of cyberattacks, including ransomware, malware, and advanced persistent threats (APTs). In this article, we’ll explore why CrowdStrike is one of the most trusted names in cybersecurity and why it’s considered a top choice for endpoint protection.
1. What is CrowdStrike?
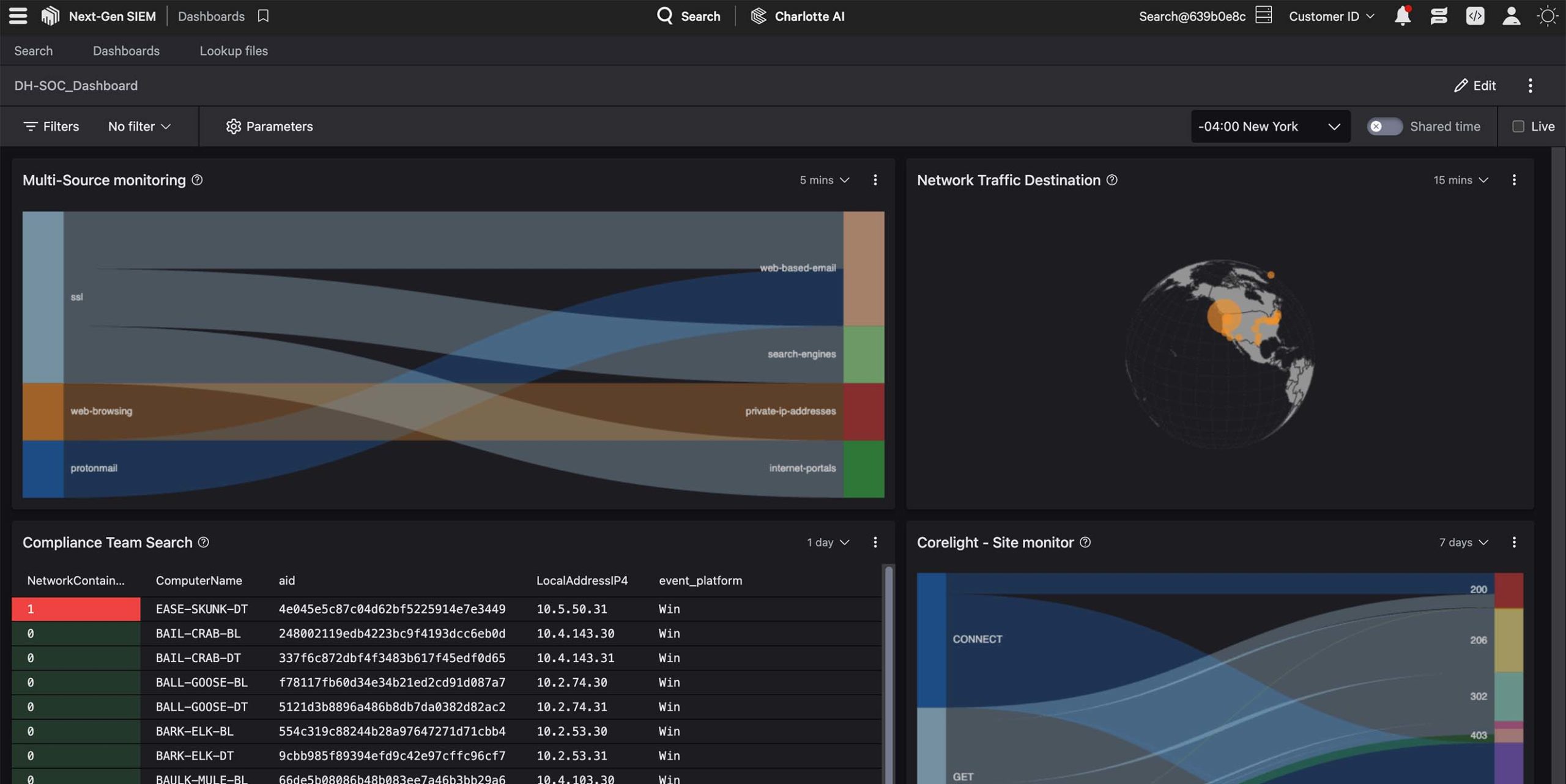
CrowdStrike is a global cybersecurity company known for its cloud-delivered endpoint protection platform. Their flagship product, CrowdStrike Falcon, leverages artificial intelligence (AI) and machine learning to provide real-time protection against cyber threats. The platform is designed to monitor endpoints continuously, detect malicious activity, and stop threats before they cause significant damage to an organization’s network and data.

Key Features of CrowdStrike Falcon:
- Cloud-native architecture: Provides scalable, real-time threat detection without the need for on-premises hardware.
- AI and Machine Learning: Leverages cutting-edge technology to identify and prevent emerging threats.
- Behavioral analysis: Monitors endpoint activity to detect suspicious behavior, rather than relying solely on signature-based detection.
- Incident response: Offers expert services for investigating and responding to security incidents.
2. Why CrowdStrike is a Popular Choice for Businesses
CrowdStrike has built a strong reputation in the cybersecurity industry due to its comprehensive and effective approach to endpoint protection. Here are some of the reasons why it is so widely adopted:

A. Advanced Threat Detection and Prevention
CrowdStrike uses machine learning and behavioral analytics to detect and prevent a wide range of threats. Unlike traditional antivirus solutions, which often rely on known malware signatures, CrowdStrike’s Falcon platform is able to detect previously unknown or zero-day threats by identifying suspicious behaviors in real-time.
B. Cloud-based Architecture
Being a cloud-native platform, CrowdStrike’s Falcon operates without the need for heavy on-premises infrastructure. This allows businesses to rapidly deploy security without worrying about managing or scaling physical hardware. The cloud-based design also ensures that updates and new security features are automatically applied, ensuring continuous protection.
C. Real-Time Visibility and Continuous Monitoring
CrowdStrike provides real-time visibility into endpoint activity across an organization’s entire network. This allows businesses to quickly detect and respond to any suspicious behavior or attack. The continuous monitoring aspect ensures that threats are detected the moment they appear, even in remote or hard-to-reach endpoints.
D. Scalability
Whether you’re a small business or a large enterprise, CrowdStrike’s platform can scale to meet your needs. Its flexible architecture allows businesses to expand and secure new devices, applications, and users as their operations grow, without sacrificing performance.
E. Expert Incident Response Services
In addition to its security platform, CrowdStrike also offers expert incident response services. Their team of cybersecurity experts is available to assist organizations with investigating and mitigating security breaches. This provides peace of mind for businesses that may not have the in-house resources to deal with complex security incidents.
3. Benefits of Using CrowdStrike for Endpoint Security
A. Reduced Risk of Data Breaches
CrowdStrike’s platform is designed to identify threats early in the attack chain, preventing data breaches before they can escalate. The proactive approach significantly reduces the likelihood of a data breach, which can be costly and damaging to a company’s reputation.
B. Improved Incident Response
With real-time visibility and expert support, CrowdStrike ensures that organizations can respond to incidents quickly and efficiently. The platform’s automated detection and response capabilities allow for immediate containment of threats, minimizing the damage they may cause.
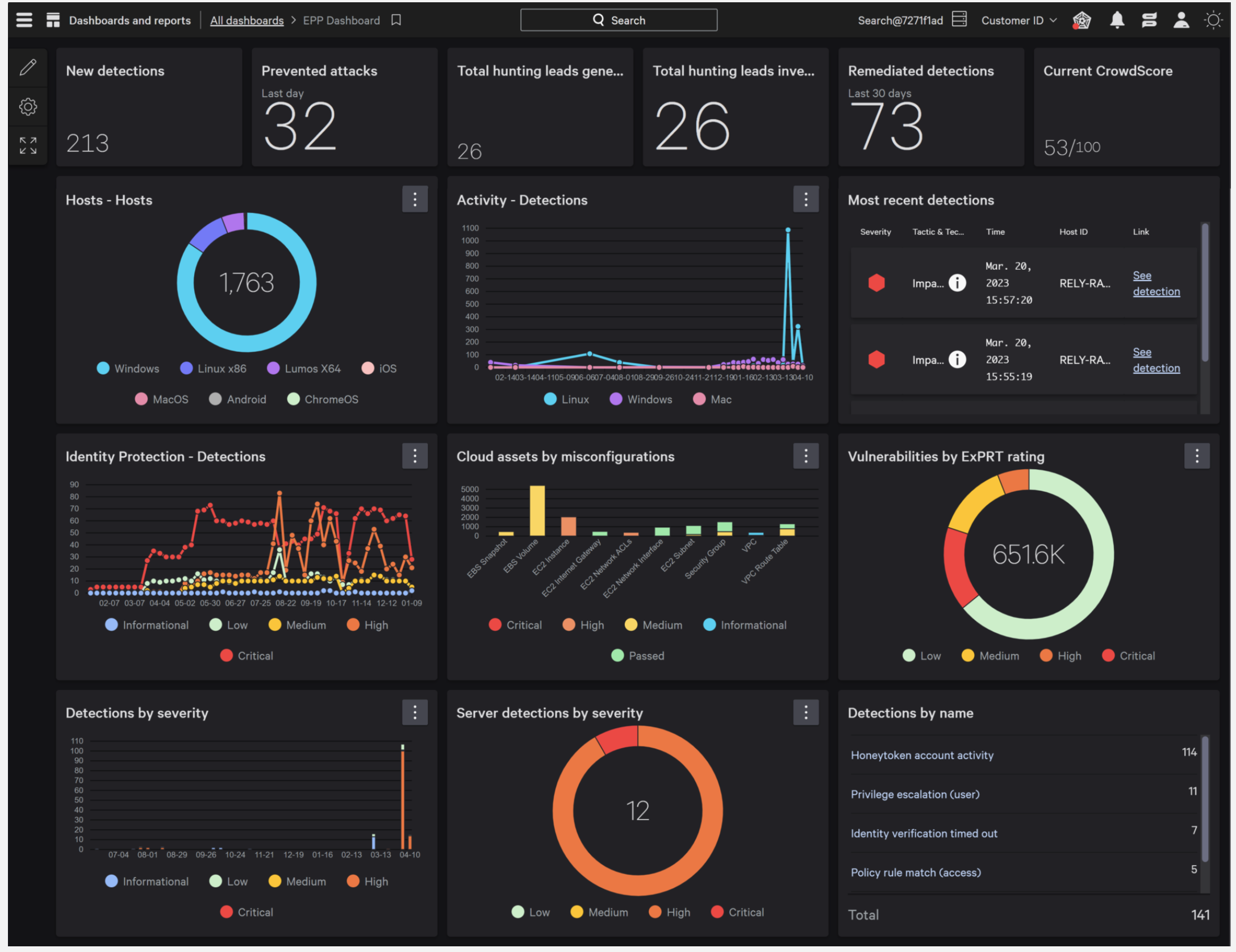
C. Cost-Effective Security
Although some may view cybersecurity as an additional cost, CrowdStrike’s platform is designed to save businesses money in the long term. By preventing data breaches and attacks, CrowdStrike reduces the financial and reputational costs that often come with cybersecurity incidents. Additionally, its cloud-native approach reduces the need for expensive infrastructure and hardware.
D. Compliance Assistance
CrowdStrike helps businesses meet compliance requirements such as GDPR, HIPAA, and PCI DSS. With its comprehensive security measures and continuous monitoring, it ensures that sensitive data is protected, helping businesses adhere to industry regulations.
4. Real-World Applications and Use Cases
CrowdStrike’s solutions have been successfully deployed across a variety of industries, including healthcare, finance, retail, and government. Here are a few examples of how CrowdStrike has helped businesses secure their systems:
- Healthcare: Hospitals and healthcare organizations rely on CrowdStrike to protect patient data and critical infrastructure from cyberattacks, especially as ransomware attacks have targeted the healthcare sector in recent years.
- Finance: Banks and financial institutions use CrowdStrike to safeguard sensitive financial data and prevent fraud. Its advanced threat detection and rapid response times help financial institutions stay ahead of evolving cybercriminal tactics.
- Retail: Retailers use CrowdStrike to prevent cyberattacks that could compromise customer data, payment systems, or eCommerce platforms, especially as online shopping continues to grow in popularity.
- Government: Government agencies use CrowdStrike to protect national security data and sensitive information from advanced persistent threats and nation-state actors.

5. How to Get Started with CrowdStrike
Getting started with CrowdStrike is easy. Their platform is available through a subscription model, with tailored pricing based on your organization’s size, security needs, and the number of endpoints you need to protect.
- Step 1: Schedule a demo to see how CrowdStrike can fit into your security strategy.
- Step 2: Choose the right CrowdStrike solution based on your needs (e.g., endpoint protection, incident response).
- Step 3: Deploy CrowdStrike’s cloud-based platform across your organization.
- Step 4: Monitor, manage, and respond to threats in real-time with the help of CrowdStrike’s tools and expert services.
CrowdStrike is at the forefront of endpoint security, offering cutting-edge protection through its cloud-native, AI-driven platform. Its ability to detect and respond to advanced cyber threats in real-time, coupled with its scalability and expert incident response services, makes it a top choice for businesses across industries. If you’re looking to enhance your organization’s cybersecurity posture, CrowdStrike’s Falcon platform offers the robust, next-generation protection needed to defend against today’s evolving threats.
Interested in learning more about how CrowdStrike can protect your business from cyber threats? Contact us today for a free consultation and demo to see how our endpoint security solutions can help safeguard your digital infrastructure.