How to Secure Server APIs sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with inspirational with positive tone style and brimming with originality from the outset.
In today’s interconnected digital landscape, the security of server APIs is paramount to safeguarding sensitive data and ensuring seamless communication between systems. This guide delves into the crucial aspects of securing server APIs, highlighting the importance of robust security measures and best practices to mitigate potential risks effectively.
Understanding Server APIs Security
Securing server APIs is crucial in today’s digital landscape where data breaches and cyber attacks are prevalent. By ensuring the security of server APIs, organizations can protect sensitive data, maintain the integrity of their systems, and build trust with users.
Common Security Vulnerabilities in Server APIs
- Injection Attacks:Attackers can manipulate input data to execute malicious commands on the server, leading to data breaches.
- Broken Authentication:Weak authentication processes can allow unauthorized access to APIs, compromising sensitive information.
- Broken Object Level Authorization:Inadequate access control mechanisms can result in unauthorized users gaining access to data they should not have.
Risks Associated with Insecure Server APIs, How to Secure Server APIs
- Loss of sensitive data: Insecure server APIs can expose confidential information, leading to financial losses and reputational damage.
- Disruption of services: Cyber attacks on server APIs can disrupt operations, causing downtime and affecting user experience.
- Legal and compliance issues: Failure to secure server APIs can result in legal consequences, regulatory fines, and loss of customer trust.
Real-World Consequences of API Security Breaches
- Data breaches at major companies like Facebook, Equifax, and Uber have exposed millions of user records, leading to financial losses and damage to brand reputation.
- The Capital One breach in 2019 compromised the personal information of over 100 million customers, resulting in regulatory scrutiny and legal action against the company.
- The WannaCry ransomware attack exploited vulnerabilities in server APIs, causing widespread disruption across industries and costing billions of dollars in damages.
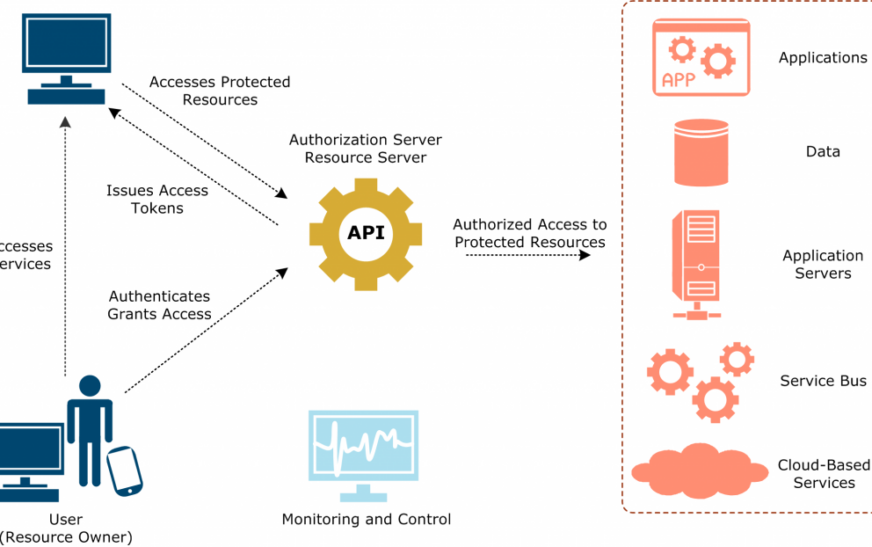
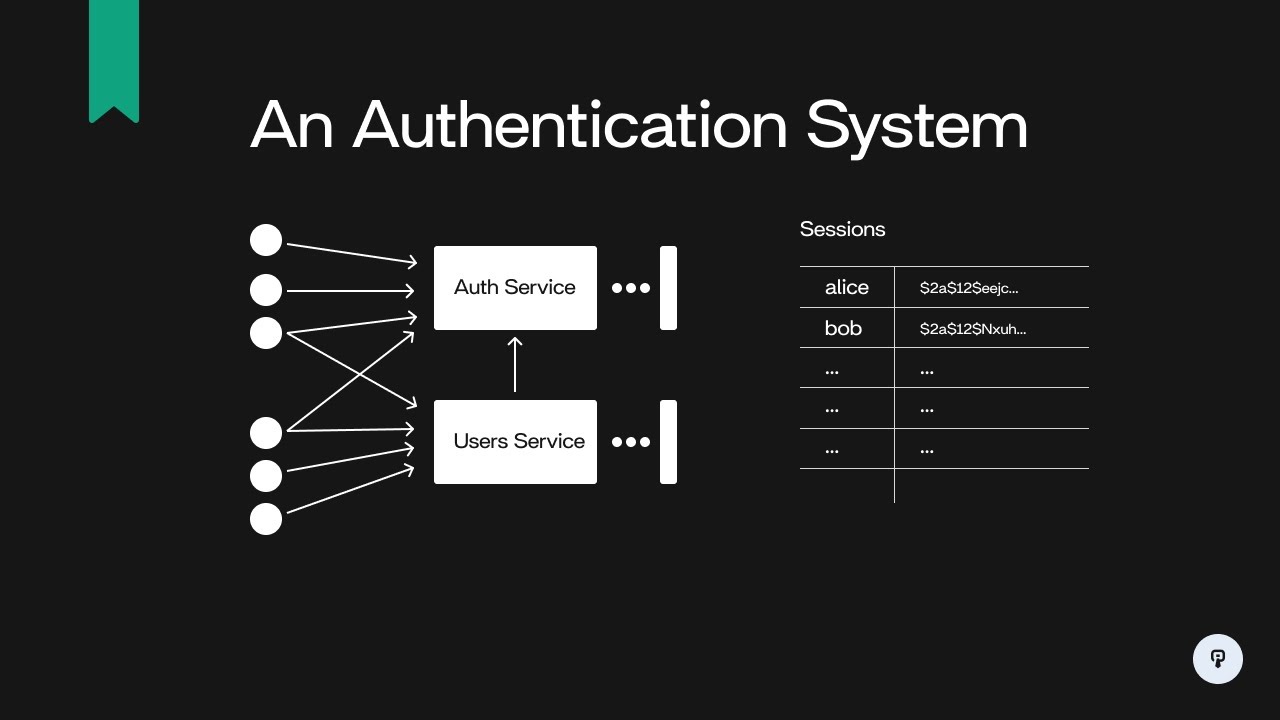
Implementing Authentication Methods: How To Secure Server APIs
Implementing strong authentication methods is crucial to ensure the security of server APIs. By incorporating robust authentication mechanisms, organizations can protect their data and prevent unauthorized access to sensitive information.
Monitoring competitor activity is crucial for staying ahead in the digital landscape. Discover how digital tools can help you keep track of your competitors effectively by visiting How Digital Tools Can Help You Monitor Competitor Activity. Stay informed and make strategic decisions to outperform your rivals!
Token-Based Authentication vs. API Keys
- Token-Based Authentication:
- Uses tokens generated by the server to authenticate users.
- Provides more security as tokens expire after a certain period.
- Offers flexibility in managing user sessions and permissions.
- API Keys:
- Consist of a unique key assigned to each user for authentication.
- Generally static and can be prone to security risks if not handled properly.
- Less secure compared to token-based authentication due to the static nature of keys.
Role of OAuth in Securing Server APIs
OAuth plays a vital role in securing server APIs by providing a standardized framework for authorization. It allows users to grant access to their resources without sharing their credentials directly. OAuth enables secure delegation of access rights and ensures that only authorized parties can interact with the API.
Setting up a game server can be a daunting task, but with the right guidance, it can be a smooth process. Check out this comprehensive guide on How to Set Up a Game Server to learn the step-by-step process and get your server up and running in no time!
Best Practices for Implementing Secure Authentication
- Use HTTPS to encrypt data transmitted between the client and server.
- Implement multi-factor authentication to add an extra layer of security.
- Regularly update and rotate API keys and tokens to mitigate the risk of unauthorized access.
- Employ rate limiting to prevent brute force attacks and unauthorized API usage.
- Audit logs to track authentication attempts and monitor for any suspicious activity.
Securing Data Transmission
Securing data transmission is crucial for server APIs to prevent unauthorized access and data breaches. By encrypting data in transit, sensitive information is protected from interception and tampering.
SSL/TLS Protocols for Enhanced Security
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) protocols are widely used to secure data transmission over the internet. These protocols establish a secure connection between the client and server, encrypting data to ensure confidentiality and integrity.
Creating compelling ad copy is key to attracting and engaging your target audience. Learn how to utilize digital tools to craft effective ad copy that drives results by reading How to Use Digital Tools to Create Effective Ad Copy.
Elevate your marketing game and maximize the impact of your advertising campaigns!
- SSL/TLS protocols use cryptographic algorithms to encrypt data, making it unreadable to unauthorized parties.
- They also provide authentication mechanisms to verify the identities of the communicating parties, preventing man-in-the-middle attacks.
- SSL/TLS certificates are used to validate the authenticity of servers, ensuring that data is transmitted securely.
HTTP vs. HTTPS for API Communications
HTTP (Hypertext Transfer Protocol) transmits data in plain text, making it vulnerable to interception. On the other hand, HTTPS (HTTP Secure) encrypts data using SSL/TLS protocols, adding a layer of security to API communications.
- Using HTTPS for API communications ensures that sensitive data, such as user credentials or payment information, is protected from eavesdropping.
- HTTPS also improves the trustworthiness of the API, as users are more likely to interact with secure endpoints.
Configuring Secure Data Transmission
To configure secure data transmission in server APIs, follow these steps:
- Obtain an SSL/TLS certificate from a trusted certificate authority.
- Install the certificate on the server hosting the API to enable HTTPS.
- Update API endpoints to use HTTPS URLs for secure data transmission.
- Implement proper encryption protocols and algorithms to protect data in transit.
- Regularly monitor and update SSL/TLS configurations to maintain security standards.
Preventing Injection Attacks
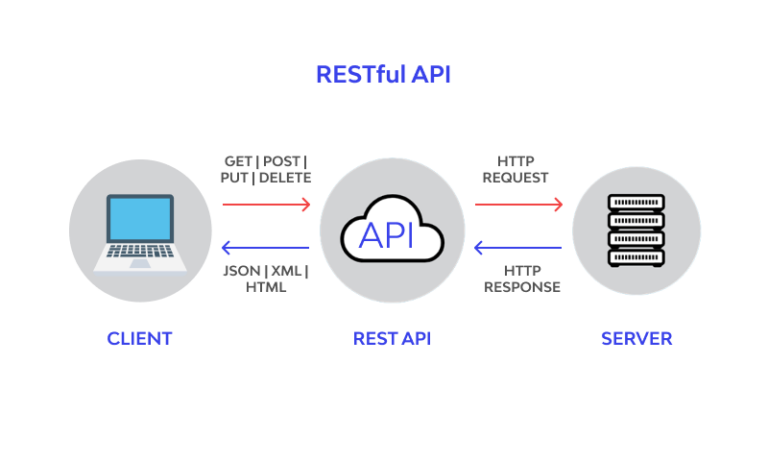
Injection attacks are a common threat to server APIs, allowing malicious actors to insert and execute unauthorized code. It is crucial to understand the types of injection attacks and how to prevent them effectively.
Mitigating SQL Injection Vulnerabilities
SQL injection is a type of attack where malicious SQL statements are inserted into an entry field for execution. To mitigate SQL injection vulnerabilities, follow these best practices:
- Use parameterized queries to prevent user input from being interpreted as SQL commands.
- Implement input validation to restrict the type and length of user input.
- Regularly update and patch your database management system to address any known vulnerabilities.
Preventing NoSQL Injection
NoSQL injection is a similar attack to SQL injection but targets NoSQL databases. To prevent NoSQL injection, consider the following best practices:
- Implement input validation and sanitization to ensure that user input does not contain malicious code.
- Use object-document mapping libraries that automatically sanitize user input.
- Limit the privileges of database users to reduce the impact of a potential injection attack.
Protecting APIs against XSS Attacks
Cross-Site Scripting (XSS) attacks involve injecting malicious scripts into web pages viewed by other users. To protect your APIs against XSS attacks, follow these techniques:
- Implement input validation to prevent the insertion of scripts into user inputs.
- Encode user input before displaying it on a web page to prevent scripts from executing.
- Use Content Security Policy (CSP) headers to restrict the sources from which scripts can be loaded.
End of Discussion
As we conclude this exploration into securing server APIs, it becomes evident that a proactive approach to security is essential in safeguarding valuable data and maintaining the integrity of API communications. By implementing the strategies Artikeld in this guide, organizations can bolster their defenses and create a resilient framework against potential security threats.