How to Monitor Server Security Incidents is crucial in safeguarding your data and systems from potential threats. By understanding the importance of monitoring, exploring various tools and best practices, you can ensure a secure environment for your servers.
Overview of Server Security Incidents Monitoring
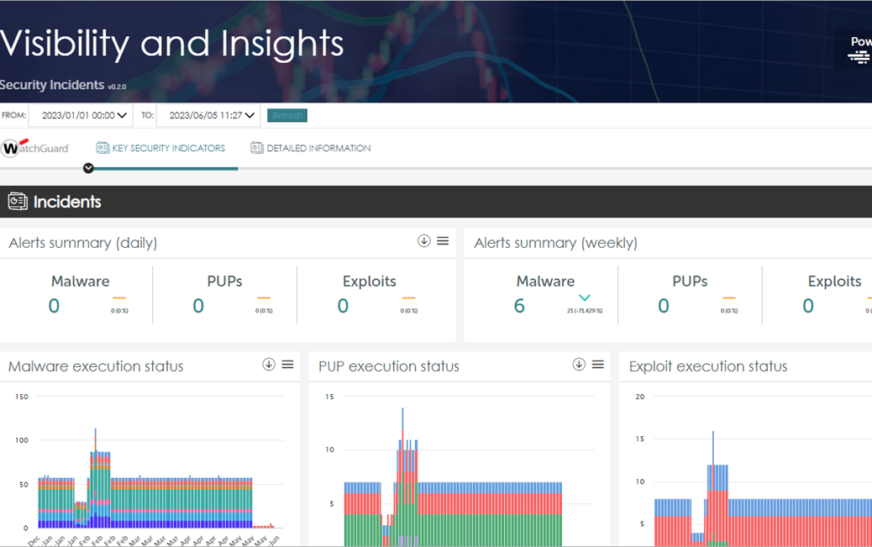
Monitoring server security incidents is crucial in maintaining the integrity and confidentiality of data stored on servers. By actively monitoring for security incidents, organizations can detect and respond to potential threats before they escalate into larger issues.
Common Types of Security Incidents
- Malware Infections: Malicious software designed to infiltrate and damage servers.
- Unauthorized Access: Intruders gaining access to sensitive information without permission.
- Denial of Service Attacks: Overwhelming servers with traffic to disrupt normal operations.
- Data Breaches: Unauthorized access leading to the exposure of confidential data.
Consequences of Not Monitoring Server Security Incidents
Failure to monitor server security incidents can have severe consequences for organizations, including:
-
Data Loss: Loss of critical data due to security breaches.
-
Financial Loss: Costs associated with recovering from security incidents and potential legal liabilities.
-
Reputation Damage: Loss of trust from customers and stakeholders due to data breaches.
Servers play a vital role in web hosting by storing, processing, and delivering website content to users. Understanding The Role of Servers in Web Hosting is key to providing a seamless browsing experience. With reliable servers, you can ensure fast loading times and secure data storage for your website.
-
Regulatory Fines: Non-compliance with data protection regulations resulting in fines and penalties.
Tools and Software for Monitoring Server Security
When it comes to monitoring server security incidents, there are various tools and software available that can help in detecting and responding to potential threats. These tools play a crucial role in ensuring the safety and integrity of your server environment.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are tools that monitor network traffic for suspicious activity and alert administrators when potential security incidents are detected. They can identify known attack signatures or abnormal behavior that may indicate a security breach.
- Snort: Snort is a popular open-source IDS that uses signature-based detection to identify known threats.
- Suricata: Suricata is another open-source IDS that offers both signature-based and anomaly-based detection capabilities.
Security Information and Event Management (SIEM)
SIEM tools collect, analyze, and correlate security event data from various sources to provide a comprehensive view of the security posture of your server environment. They can help in identifying patterns and trends that may indicate a security incident.
- Splunk: Splunk is a SIEM tool that can ingest and analyze large volumes of security data to detect and respond to security incidents in real-time.
- LogRhythm: LogRhythm is another SIEM tool that offers advanced analytics and automation capabilities for threat detection and response.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) tools focus on monitoring and securing individual endpoints, such as servers and workstations, against advanced threats and malware. They provide visibility into endpoint activities and enable quick response to security incidents.
- CrowdStrike Falcon: CrowdStrike Falcon is an EDR platform that uses machine learning and behavioral analytics to detect and respond to endpoint threats.
- CylancePROTECT: CylancePROTECT is another EDR solution that leverages artificial intelligence to prevent and detect malware on endpoints.
Using automated monitoring tools like IDS, SIEM, and EDR can significantly enhance your server security posture by detecting and responding to security incidents in a timely manner.
Best Practices for Monitoring Server Security Incidents
When it comes to monitoring server security incidents, there are several best practices that can help you stay ahead of potential threats and ensure the safety of your data. Setting up alerts and notifications, creating a response plan, and conducting regular security audits are key components of a robust security monitoring strategy.
Improving server uptime is crucial for a smooth online experience. By following the tips in How to Improve Server Uptime , you can ensure that your website is always accessible to users. Implementing regular maintenance and monitoring can help prevent downtime and keep your server running efficiently.
Setting up Alerts and Notifications
One of the first steps in effectively monitoring server security incidents is to set up alerts and notifications for any suspicious activity. This can include unusual login attempts, unauthorized access to sensitive files, or any other behavior that may indicate a security breach.
Scaling your server infrastructure is essential as your business grows. Check out How to Scale Your Server Infrastructure to learn how to expand your server capacity to accommodate increasing traffic. By optimizing your resources and utilizing cloud services, you can effectively scale your server infrastructure.
By configuring alerts to trigger when specific criteria are met, you can quickly identify and respond to potential threats before they escalate.
Creating a Response Plan
In addition to setting up alerts, it’s essential to have a well-defined response plan in place for when security incidents are identified. This plan should Artikel the steps to be taken in the event of a breach, including who will be responsible for managing the incident, how communication will be handled, and what actions will be taken to contain and mitigate the impact of the incident.
By having a clear and concise response plan, you can ensure a swift and effective response to any security threats.
Importance of Regular Security Audits
Regular security audits are crucial for monitoring server security and identifying potential vulnerabilities before they can be exploited by malicious actors. By conducting thorough audits of your systems and networks on a regular basis, you can proactively identify and address any security weaknesses, ensuring that your data remains safe and secure.
These audits can also help you stay compliant with industry regulations and best practices, further enhancing the overall security of your server environment.
Real-Time Monitoring vs. Periodic Monitoring: How To Monitor Server Security Incidents
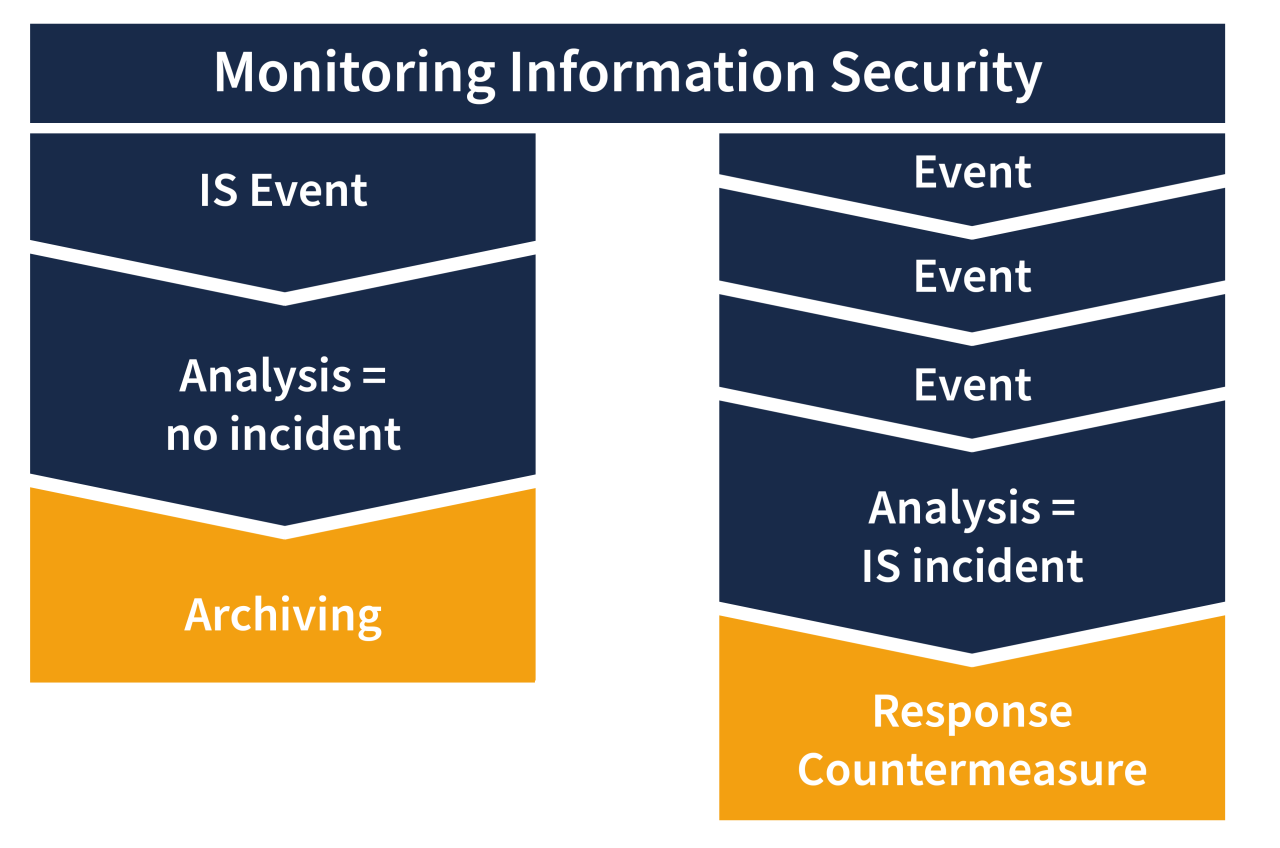
Real-time monitoring and periodic monitoring are two common approaches to monitoring server security incidents. Each method has its own advantages and disadvantages, depending on the specific needs and requirements of the organization.
Real-Time Monitoring, How to Monitor Server Security Incidents
Real-time monitoring involves continuous monitoring of server activities to detect and respond to security incidents as they occur. This approach provides immediate visibility into any unauthorized access or suspicious behavior on the server.
- Advantages:
- Immediate detection of security incidents
- Quick response time to mitigate risks
- Enhanced security posture by preventing potential breaches
- Disadvantages:
- Higher resource utilization due to continuous monitoring
- Potential for false positives leading to unnecessary alerts
- Increased complexity in managing real-time alerts
Periodic Monitoring
Periodic monitoring involves scheduled checks and reviews of server logs and activities at regular intervals. This approach allows organizations to have a comprehensive view of security incidents over time and identify patterns or trends.
- Advantages:
- Lower resource utilization compared to real-time monitoring
- Ability to analyze historical data for trend identification
- Less complexity in managing monitoring activities
- Disadvantages:
- Delayed detection of security incidents
- Risk of missing critical security events during monitoring gaps
- Limited visibility into immediate threats
Examples of when to use real-time monitoring include high-risk environments where immediate response is crucial, such as financial institutions or government agencies. On the other hand, periodic monitoring may be more suitable for organizations with lower security risks or limited resources, where regular reviews can still provide effective security oversight.
Closure
In conclusion, staying vigilant and proactive in monitoring server security incidents is key to maintaining a secure infrastructure. By implementing the right tools, following best practices, and choosing the appropriate monitoring approach, you can effectively protect your servers from cyber threats.