How to Implement Serverless Architecture sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. Dive into the world of serverless architecture and unleash the potential it holds for your projects.
Overview of Serverless Architecture
Serverless architecture is a cloud computing model where the cloud provider manages the infrastructure and automatically allocates resources as needed. Key characteristics include scalability, cost efficiency, and reduced operational complexity.One of the main benefits of implementing a serverless architecture is the ability to focus on developing and deploying code without having to worry about managing servers or infrastructure.
This leads to faster development cycles and increased agility for organizations.Common use cases where serverless architecture is a good fit include event-driven applications, real-time data processing, and microservices. By leveraging serverless computing, organizations can scale their applications easily, reduce costs, and improve overall performance.
Key Components of Serverless Architecture: How To Implement Serverless Architecture
Serverless architecture is built on several key components that work together seamlessly to provide scalable and efficient solutions for modern applications. Let’s explore the main components involved in serverless architecture and their roles in the overall system.
Organize and streamline your digital assets with the help of Top Digital Tools for Managing Digital Assets. These tools will not only save you time and effort but also ensure that your digital assets are easily accessible and well-maintained for seamless workflow.
Functions as a Service (FaaS)
Functions as a Service, or FaaS, is a core component of serverless architecture that allows developers to write and deploy code in the form of functions. These functions are executed in response to specific events, such as HTTP requests or database changes.
FaaS platforms, like AWS Lambda, Google Cloud Functions, and Azure Functions, handle the infrastructure management, scaling, and execution of these functions automatically, enabling developers to focus on writing code without worrying about server management.
Embrace the power of technology with The Best Digital Tools for Performance Marketing and unlock new opportunities to boost your business performance. These tools are designed to help you reach your target audience effectively and maximize your marketing efforts.
Event Triggers
Event triggers are mechanisms that initiate the execution of functions in a serverless architecture. These triggers can be various types of events, such as HTTP requests, database changes, file uploads, or scheduled tasks. When an event occurs, the corresponding function is invoked to process the event and generate a response.
Event triggers enable the seamless integration of different services and components within a serverless application, allowing for event-driven and reactive programming models.
Serverless Frameworks
Serverless frameworks provide a set of tools, libraries, and services to simplify the development, deployment, and management of serverless applications. These frameworks abstract away the complexities of serverless architecture and offer features like function composition, deployment automation, monitoring, and debugging.
Popular serverless frameworks, such as Serverless Framework, AWS SAM, and Azure Serverless, help developers streamline their workflow and accelerate the development process by providing reusable templates and built-in integrations with various cloud services.
Scalability and Elasticity, How to Implement Serverless Architecture
Scalability and elasticity are inherent characteristics of serverless architecture that enable applications to automatically adjust their resources based on demand. Serverless platforms dynamically allocate resources to handle incoming requests and scale up or down in real-time to accommodate fluctuating workloads.
This scalability and elasticity ensure high availability, performance, and cost efficiency for serverless applications, as resources are only provisioned and billed based on actual usage.
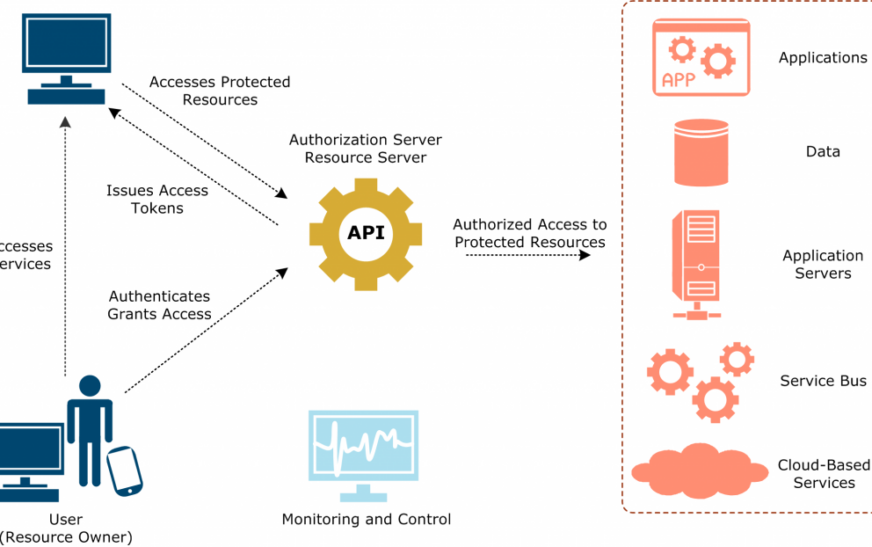
Third-Party Services and APIs
Serverless applications often rely on third-party services and APIs to extend their functionality and integrate with external systems. These services can include databases, messaging queues, authentication providers, payment gateways, and more. By leveraging existing APIs and services, developers can offload common tasks and focus on building the core business logic of their applications.
Gain valuable insights and optimize your social media strategy with The Best Digital Tools for Social Media Analytics. These tools will provide you with in-depth analytics and metrics to track your social media performance and enhance your online presence.
Serverless platforms offer seamless integration with a wide range of third-party services through built-in connectors and libraries, enabling developers to quickly add new features and capabilities to their applications.
How to Design Serverless Applications
Designing serverless applications involves careful planning and consideration to ensure efficiency, scalability, and cost-effectiveness. By following best practices and optimizing the design, you can create robust serverless applications that meet your business needs.
Steps for Designing a Serverless Application
- Define the requirements and goals of the application to determine the necessary components and functionality.
- Choose the right cloud provider and services based on your specific needs and budget.
- Design the architecture with scalability in mind, using event-driven design and microservices for flexibility.
- Implement security measures to protect your application and data from potential threats.
- Test the application thoroughly to identify and address any potential issues before deployment.
Best Practices for Efficient and Scalable Serverless Applications
- Follow the principles of serverless computing, such as pay-as-you-go pricing and auto-scaling, to optimize resource utilization.
- Use managed services provided by cloud providers to offload infrastructure management tasks and focus on application development.
- Implement monitoring and logging to track performance metrics and troubleshoot any issues that may arise.
Tips for Optimizing Serverless Application Design for Cost-effectiveness
- Optimize code for performance to reduce execution time and minimize costs associated with function invocations.
- Use caching mechanisms to store frequently accessed data and reduce the need for repeated computations.
- Implement resource allocation strategies to ensure that you are only paying for the resources you actually use.
Implementation Steps for Serverless Architecture
Implementing serverless architecture involves migrating existing applications or designing new projects with a focus on scalability and cost-effectiveness. Let’s explore the key steps and considerations in this process.
Migrating an Existing Application to Serverless Architecture
- Assess the current application: Understand the functionalities, dependencies, and resource requirements of the existing application.
- Identify serverless-compatible components: Determine which parts of the application can be modularized and run as serverless functions.
- Refactor and rearchitect: Modify the codebase to fit the serverless model, breaking down monolithic structures into smaller, independent functions.
- Integrate with cloud services: Utilize managed services provided by cloud providers for functions like storage, databases, and authentication.
- Testing and monitoring: Implement robust testing procedures and monitoring tools to ensure the performance and reliability of the migrated application.
Challenges and Considerations in Implementing Serverless Architecture
- Cold start latency: Address the potential delay in function execution caused by cold starts when a function is invoked for the first time.
- Vendor lock-in: Be aware of the dependency on a specific cloud provider and consider strategies to mitigate risks associated with vendor lock-in.
- Security and compliance: Implement security best practices and ensure compliance with regulations when working with sensitive data in a serverless environment.
Step-by-Step Guide for Implementing Serverless Architecture in a New Project
- Define project requirements: Clearly Artikel the objectives, functionalities, and scalability needs of the new project.
- Choose a cloud provider: Select a cloud platform that aligns with the project requirements and offers robust serverless capabilities.
- Design serverless architecture: Break down the project into smaller, independent functions and design the workflow of how these functions interact.
- Develop and deploy functions: Write the code for individual functions, test them locally, and deploy them to the cloud platform.
- Monitor and optimize: Continuously monitor the performance of functions, optimize resource allocation, and refine the architecture based on usage patterns.
Security Considerations in Serverless Architecture
Security is a critical aspect of serverless applications as they rely on third-party services to manage server-side logic and infrastructure. Ensuring the security of serverless applications and data is essential to protect sensitive information and prevent unauthorized access.
Importance of Security in Serverless Applications
- Serverless applications are vulnerable to various security threats due to the dynamic nature of the environment.
- Securing serverless applications helps in maintaining data integrity and confidentiality.
- Failure to address security concerns can lead to data breaches and compromise the overall system.
Common Security Risks in Serverless Architecture
- Lack of proper access controls: Inadequate permission settings can result in unauthorized access to resources.
- Insecure APIs: Exposing sensitive data through APIs can lead to data leaks and security breaches.
- Data injection attacks: Malicious inputs can manipulate the serverless functions and compromise the system.
Best Practices for Securing Serverless Applications and Data
- Implement robust authentication and authorization mechanisms to control access to resources.
- Encrypt sensitive data at rest and in transit to prevent unauthorized access.
- Regularly monitor and audit serverless functions for any security vulnerabilities or anomalies.
- Utilize security tools and services to enhance the overall security posture of the serverless applications.
Ultimate Conclusion
Embrace the power of serverless architecture and revolutionize the way you approach application development. With the right knowledge and strategies, you can seamlessly implement serverless architecture and take your projects to new heights of efficiency and scalability.