Delving into How to Configure a Server Firewall, this introduction immerses readers in a unique and compelling narrative, providing insights into the importance and process of configuring a server firewall.
Understanding the fundamentals of server firewall configuration, the differences between inbound and outbound rules, and the best practices involved sets the stage for a comprehensive exploration ahead.
Introduction to Server Firewalls
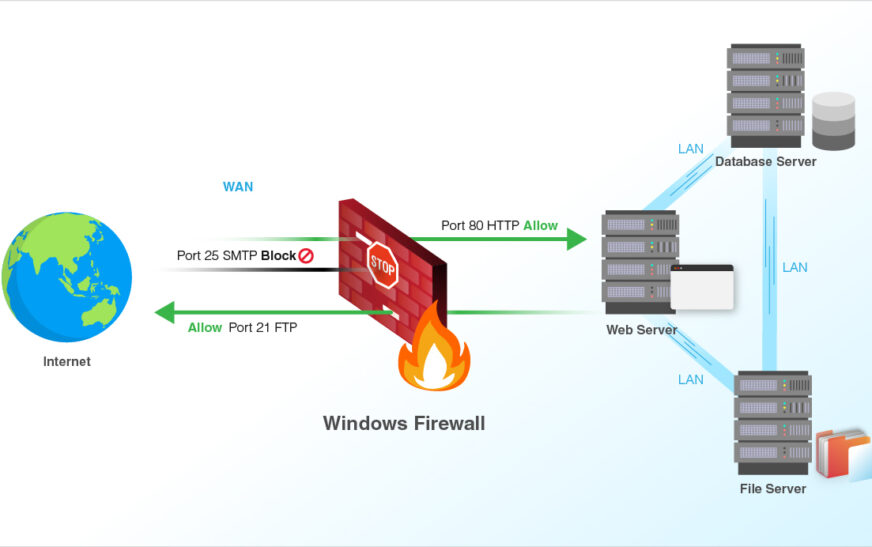
Server firewalls are essential components of network security that act as a barrier between a server and potential threats from the internet. They help prevent unauthorized access, protect sensitive data, and ensure the integrity and availability of the server.
Effortlessly collaborate online with the help of the Top Digital Tools for Online Collaboration. Stay connected with your team, share ideas, and work seamlessly together no matter where you are.
Types of Server Firewalls
- Packet Filtering Firewalls: These examine packets of data and make decisions based on predefined rules.
- Proxy Firewalls: These act as intermediaries between internal and external networks, inspecting incoming and outgoing traffic.
- Stateful Inspection Firewalls: These track the state of active connections and make decisions based on the context of the traffic.
Configuring a server firewall is crucial to tailor the security settings to the specific needs of the server and the network it operates in. Proper configuration can help minimize security vulnerabilities, reduce the risk of cyber attacks, and ensure the smooth functioning of the server.
Embrace the power of digital tools in creating a cohesive brand identity with How Digital Tools Can Help You Create a Cohesive Brand Identity. These tools provide endless possibilities to showcase your brand’s unique voice and values.
Understanding Server Firewall Configuration
Firewalls play a crucial role in protecting servers from unauthorized access and malicious threats. Configuring a server firewall involves setting up rules and policies to control the incoming and outgoing network traffic.Inbound and Outbound Rules:
Difference between Inbound and Outbound Rules, How to Configure a Server Firewall
- Inbound Rules:Inbound rules are applied to incoming traffic from external sources to the server. These rules determine what type of traffic is allowed to reach the server, such as web requests or file transfers.
- Outbound Rules:Outbound rules, on the other hand, govern the outgoing traffic from the server to external destinations. They control what data can leave the server, such as responses to incoming requests or data backups.
Application and Prioritization of Firewall Rules:
Application and Prioritization of Firewall Rules
- Firewall rules are applied based on a set of criteria, such as source/destination IP addresses, ports, protocols, and application types.
- Rules can be prioritized to ensure that certain rules take precedence over others. This allows for fine-tuning of the firewall configuration to meet specific security requirements.
- Firewall policies can be created to group related rules together for easier management and enforcement.
Setting Up a Server Firewall
Setting up a server firewall is essential to protect your system from unauthorized access and potential security threats. Follow these steps to configure your server firewall effectively.
Take your live streaming game to the next level with The Best Digital Tools for Live Streaming. From high-quality video production to engaging with your audience in real-time, these tools are essential for success in the digital world.
Accessing Server Firewall Settings
To access the server firewall settings, follow these steps:
- Log in to your server using your admin credentials.
- Locate the firewall settings in the server management interface.
- Click on the firewall settings to view and modify the rules.
Adding or Removing Firewall Rules
When it comes to adding or removing firewall rules, here’s what you need to do:
- To add a new rule, specify the source, destination, port, and protocol for the traffic you want to allow or block.
- To remove a rule, simply select the rule you want to delete and confirm the action.
- Review the existing rules periodically and adjust them based on your server’s security requirements.
Best Practices for Configuring a Server Firewall
Configuring a server firewall requires attention to detail and adherence to best practices to ensure optimal security. Here are some tips to keep in mind:
- Restrict access to only necessary services and ports to minimize potential vulnerabilities.
- Regularly update firewall rules based on changes in your network environment or security policies.
- Implement a logging mechanism to monitor firewall activity and detect any suspicious behavior.
- Consider using application-specific firewalls in addition to the server firewall for enhanced protection.
- Test firewall rules periodically to verify their effectiveness and make adjustments as needed.
Testing and Verifying Firewall Configuration: How To Configure A Server Firewall
After setting up your server firewall, it is crucial to test and verify that the configuration is correct. This ensures that your server is secure and protected from potential threats.
Methods to Test Firewall Configuration
- Perform port scans to check which ports are open and closed.
- Use online tools like Nmap to identify any vulnerabilities in the firewall rules.
- Simulate different types of attacks to see how the firewall responds.
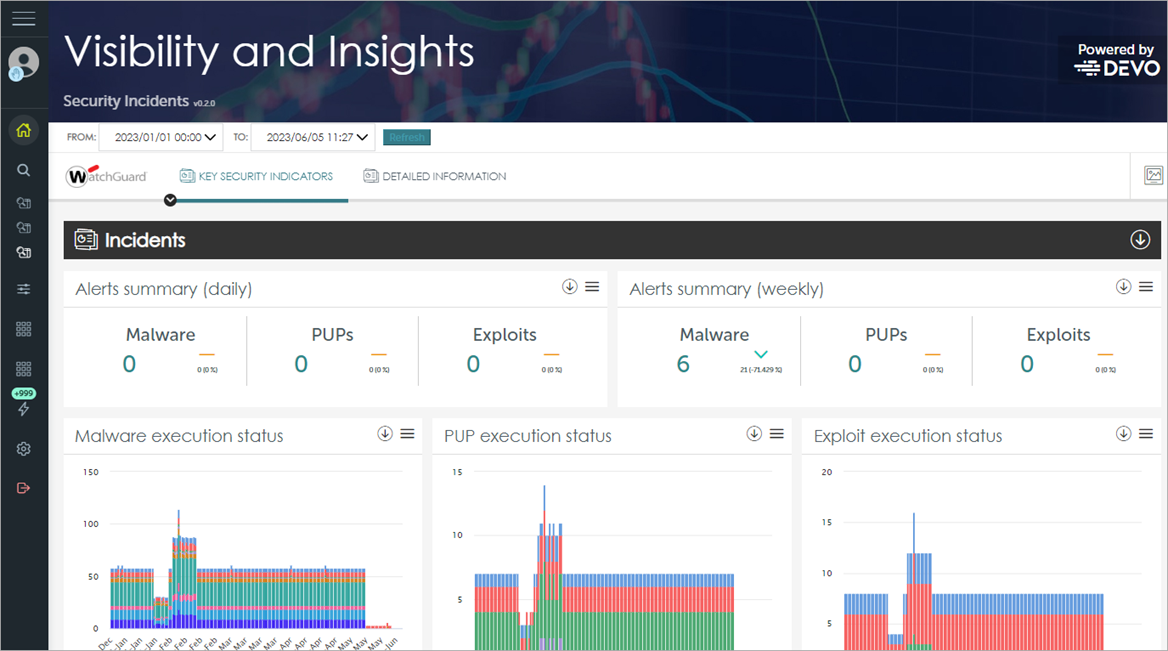
Monitoring Firewall Logs
Monitoring firewall logs is essential to detect any unusual activity or potential security breaches. Regularly reviewing these logs can help you identify and respond to threats in a timely manner.
Importance of Regular Firewall Configuration Audits
Regular firewall configuration audits are necessary to ensure that your security measures are up to date and effective. By conducting audits periodically, you can identify any weaknesses or misconfigurations that could leave your server vulnerable to attacks.
Closing Notes
In conclusion, mastering the art of server firewall configuration is crucial for safeguarding your system against potential threats. Regular audits and monitoring ensure optimal security, making it a vital aspect of maintaining a secure server environment.