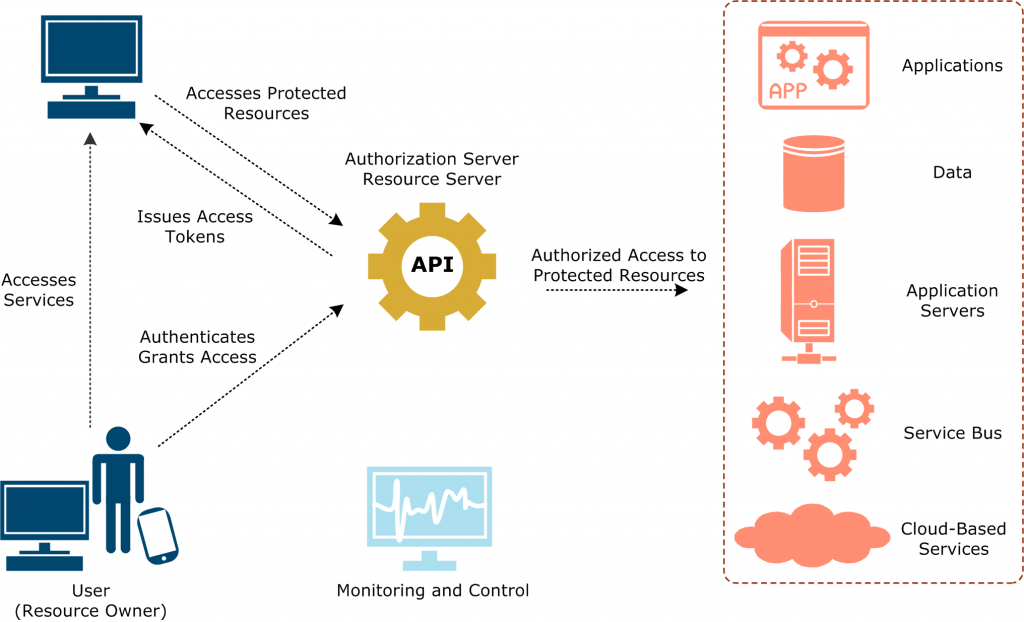
How to Implement Server-Based Encryption delves into the crucial aspects of securing data through encryption on servers, offering insights and practical tips for a successful implementation.
From understanding the significance of server-based encryption to navigating encryption algorithms and key management, this guide equips you with the knowledge to enhance your data security measures effectively.
Overview of Server-Based Encryption: How To Implement Server-Based Encryption
Server-Based Encryption is a method used to protect sensitive data by encrypting it on the server before storing or transmitting it. This is crucial for enhancing data security and preventing unauthorized access to confidential information.Server-Based Encryption works by encrypting data at the server level, ensuring that only authorized users with the encryption keys can access the information.
Setting up a web server can be a daunting task, but with the right guidance, it can be a smooth process. Follow this detailed guide on How to Set Up a Web Server to ensure your website runs smoothly and efficiently.
This adds an extra layer of security to sensitive data, making it more difficult for cybercriminals to steal or manipulate.
Importance of Server-Based Encryption
- Financial Data: Server-Based Encryption can protect financial information such as credit card numbers, bank account details, and transaction records.
- Personal Identifiable Information (PII): Sensitive data like social security numbers, addresses, and phone numbers can be safeguarded using server-based encryption.
- Healthcare Records: Patient medical history, treatment plans, and other healthcare data can be securely stored and transmitted through server-based encryption.
Implementing Server-Based Encryption
Implementing server-based encryption is a crucial step in ensuring the security of sensitive data. It involves a series of steps and considerations to guarantee a successful implementation.
Steps Involved in Implementing Server-Based Encryption, How to Implement Server-Based Encryption
- Assess Data Sensitivity: Identify the data that needs to be encrypted based on its sensitivity and potential impact if compromised.
- Choose Encryption Algorithm: Select a strong encryption algorithm that meets industry standards and is suitable for the type of data being protected.
- Generate Encryption Keys: Create and securely store encryption keys that will be used to encrypt and decrypt data on the server.
- Implement Encryption Mechanism: Integrate encryption mechanisms into the server infrastructure to ensure that data is encrypted at rest and in transit.
- Test and Validate: Thoroughly test the encryption implementation to ensure that data remains secure and accessible only to authorized users.
- Monitor and Update: Regularly monitor the encryption system for any vulnerabilities or issues, and update it as needed to maintain security.
Key Considerations Before Implementing Server-Based Encryption
- Compliance Requirements: Ensure that the encryption implementation aligns with regulatory requirements and industry best practices.
- Performance Impact: Evaluate the potential performance impact of encryption on server operations and implement measures to mitigate any slowdowns.
- Key Management: Establish robust key management practices to safeguard encryption keys and prevent unauthorized access.
- User Access Controls: Implement strict user access controls to limit the number of users who can decrypt encrypted data on the server.
Best Practices for a Successful Implementation of Server-Based Encryption
- Regularly Update Encryption Protocols: Stay up-to-date with the latest encryption protocols and technologies to enhance security and protect against evolving threats.
- Encrypt Data End-to-End: Implement end-to-end encryption to ensure that data is protected throughout its entire lifecycle, from storage to transmission.
- Train Employees: Provide training to employees on encryption best practices and the importance of data security to prevent human errors that could compromise encryption.
- Perform Regular Security Audits: Conduct regular security audits to identify vulnerabilities in the encryption system and address them promptly to maintain data integrity.
Choosing Encryption Algorithms
When it comes to selecting encryption algorithms for server-based encryption, it is crucial to consider various factors to ensure the security and efficiency of data protection. The choice of encryption algorithm can significantly impact the overall security of your server and the data it holds.
Let’s explore the different encryption algorithms suitable for server-based encryption and the important considerations to keep in mind.
When it comes to server room design, there are certain best practices that can make a significant impact on the efficiency and functionality of your servers. Learn more about these practices in this informative article on The Best Practices for Server Room Design to create an optimal environment for your servers.
Comparison of Encryption Algorithms
- Advanced Encryption Standard (AES): Widely used and highly secure, with key lengths of 128, 192, or 256 bits.
- Rivest Cipher (RC): Including RC4, RC5, and RC6, known for simplicity and speed but may have vulnerabilities.
- Data Encryption Standard (DES): An older algorithm, now deemed insecure due to its small key size.
- Triple Data Encryption Standard (3DES): Offers improved security over DES by applying the algorithm three times.
Factors to Consider in Algorithm Selection
- Security Strength: Ensure the algorithm provides a high level of security to protect sensitive data from potential threats.
- Performance Impact: Consider the processing speed and efficiency of the algorithm to minimize any performance impacts on server operations.
- Compatibility: Choose an algorithm that is compatible with your existing systems and infrastructure to ensure seamless integration.
- Regulatory Compliance: Verify that the selected algorithm complies with relevant data protection regulations and standards applicable to your industry.
Importance of Regular Algorithm Updates
It is essential to periodically update encryption algorithms to stay ahead of emerging threats and vulnerabilities. Hackers are constantly developing new techniques to break encryption, making it crucial to keep algorithms up to date to maintain the security of your server and data.
Setting up a proxy server can enhance the security and performance of your network. Discover the step-by-step process of setting up a proxy server in this comprehensive guide on How to Set Up a Proxy Server and take your network to the next level.
Key Management in Server-Based Encryption
Key management plays a crucial role in server-based encryption as it involves the secure generation, storage, distribution, and disposal of encryption keys. Proper key management is essential to ensure the confidentiality and integrity of sensitive data.
Strategies for Securely Managing Encryption Keys on Servers
- Utilize Hardware Security Modules (HSMs): Hardware Security Modules provide a secure environment for storing and managing encryption keys, protecting them from unauthorized access.
- Implement Key Rotation: Regularly rotate encryption keys to limit the window of vulnerability in case a key is compromised.
- Use Strong Access Controls: Restrict access to encryption keys based on the principle of least privilege, ensuring that only authorized personnel can manage and use the keys.
- Encrypt Encryption Keys: Encrypt the encryption keys themselves to add an extra layer of protection in case they are accessed by unauthorized parties.
Challenges Associated with Key Management and How to Overcome Them
- Key Storage: Securely storing encryption keys without exposing them to potential security threats can be a challenge. Implementing secure key storage mechanisms such as HSMs can help address this issue.
- Key Distribution: Safely distributing encryption keys to authorized users or systems without interception or tampering is crucial. Using secure communication channels and encryption protocols can mitigate the risk of key interception.
- Key Lifecycle Management: Managing the entire lifecycle of encryption keys, including generation, rotation, and disposal, can be complex. Implementing automated key management systems can streamline this process and ensure compliance with security best practices.
Compliance and Regulations
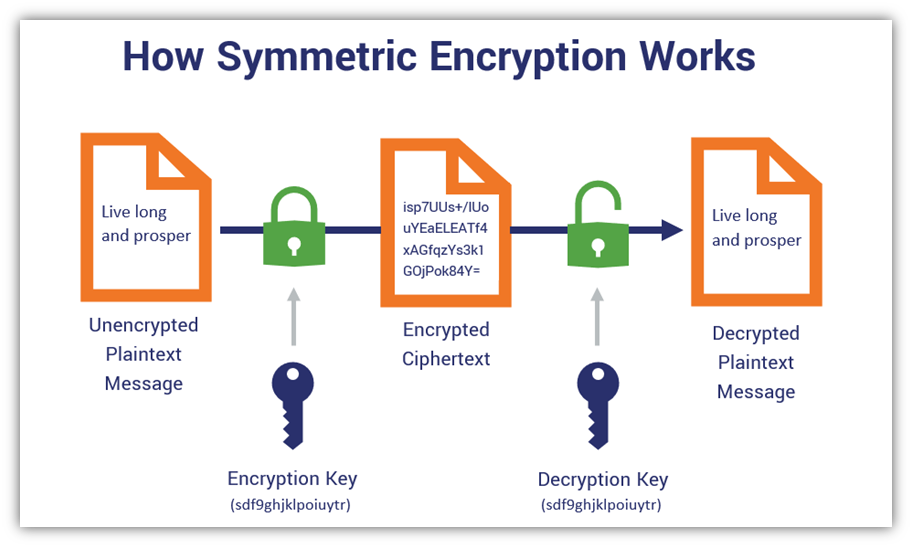
Implementing server-based encryption is crucial for organizations looking to comply with data protection regulations. By encrypting data at the server level, companies can ensure that sensitive information is secure and protected from unauthorized access.
Benefits of Server-Based Encryption for Compliance
- Server-based encryption helps organizations adhere to regulations such as GDPR (General Data Protection Regulation) by safeguarding personal data and preventing data breaches.
- It also assists in meeting HIPAA (Health Insurance Portability and Accountability Act) requirements in the healthcare industry, where protecting patient information is paramount.
- For financial institutions, server-based encryption plays a vital role in complying with regulations like PCI DSS (Payment Card Industry Data Security Standard) to protect payment card data.
Ultimate Conclusion
Embrace the power of server-based encryption to safeguard your sensitive information, meet compliance standards, and protect your organization from potential data breaches. With the right strategies and practices in place, you can establish a robust security framework that ensures the confidentiality and integrity of your data.