How to Implement Server-Based Authentication sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. In today’s digital age, securing access to servers is paramount for data protection and privacy.
This guide will walk you through the steps of implementing server-based authentication, ensuring a secure and reliable system for your organization.
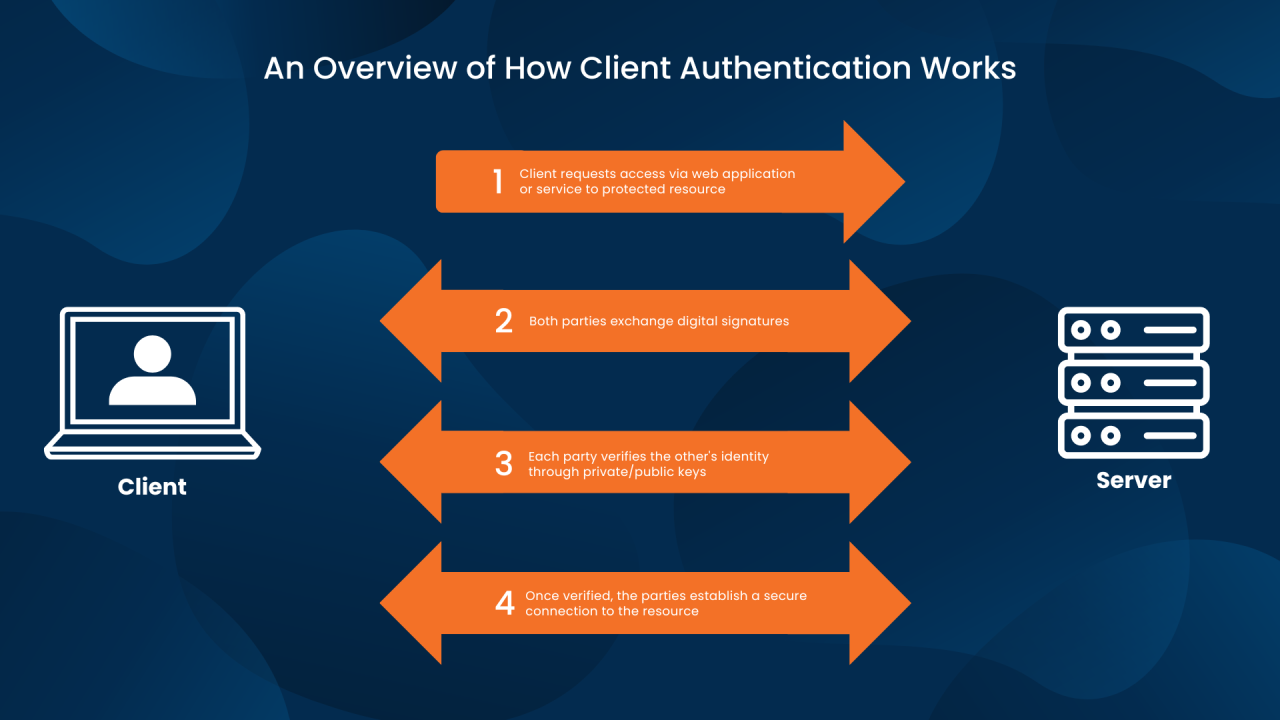
Overview of Server-Based Authentication
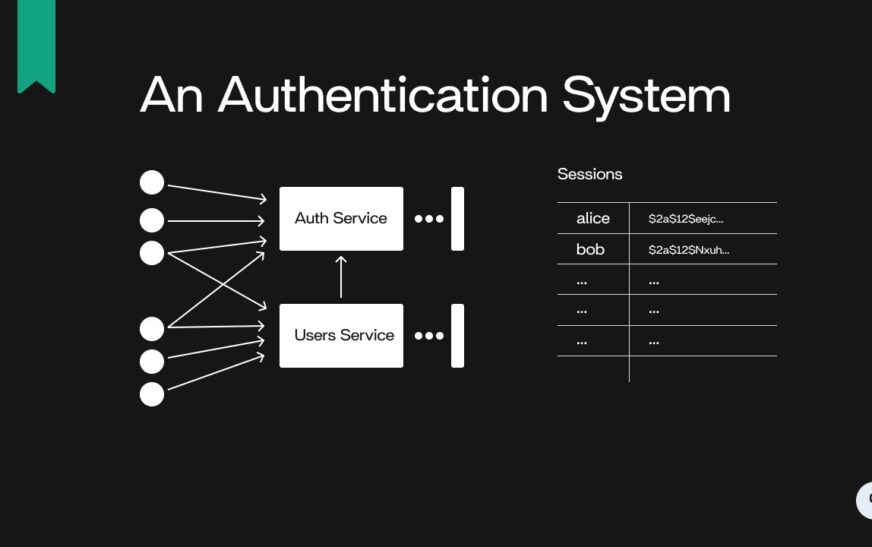
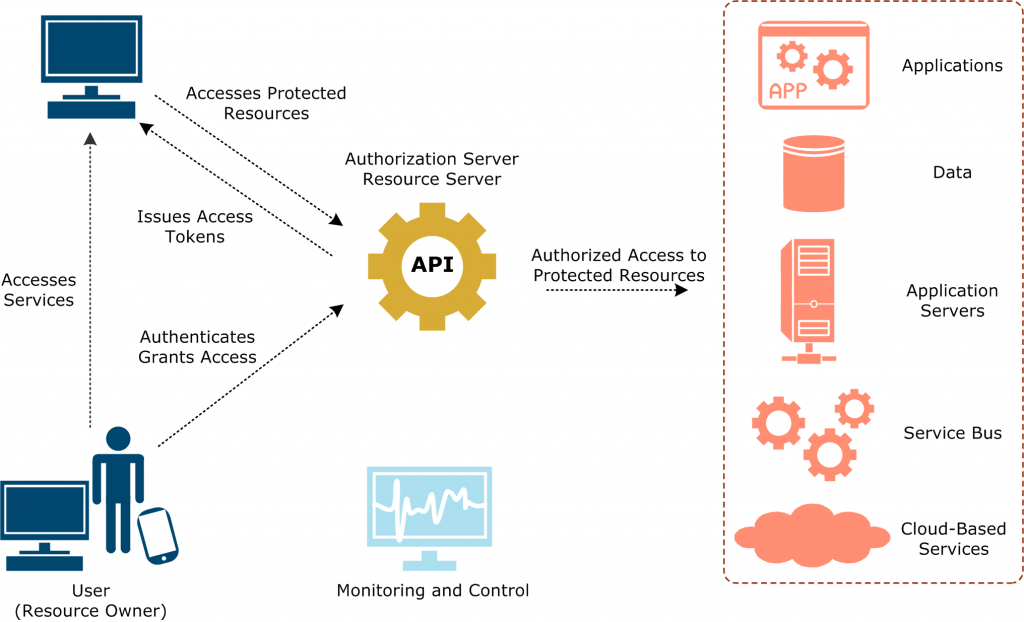
Server-Based Authentication is a method used to verify the identity of users accessing a system or application by relying on a central server to authenticate their credentials. This process involves sending user information to the server for verification before granting access to protected resources.Implementing server-based authentication is crucial for ensuring secure access to sensitive data and resources.
Optimizing server storage solutions is essential for maximizing efficiency and performance. Discover expert tips and strategies on how to make the most out of your server storage capabilities. Dive into the details of How to Optimize Server Storage Solutions and elevate your server management skills.
By centralizing the authentication process on a server, organizations can better control access permissions, monitor user activities, and enforce security policies more effectively.One of the key advantages of using server-based authentication is the ability to manage user credentials centrally, reducing the risk of unauthorized access and data breaches.
Additionally, this method allows for easier integration with existing security systems and simplifies the process of granting or revoking access privileges.
Enhanced Security
- Server-based authentication provides a centralized point of control for managing user access, reducing the risk of unauthorized access.
- By verifying user credentials on a server, organizations can detect and prevent potential security threats more effectively.
- Centralized authentication allows for the enforcement of strong password policies and multi-factor authentication, enhancing overall security measures.
Scalability and Integration
- Server-based authentication can easily scale to accommodate a growing number of users or resources without compromising security.
- Integration with existing security systems and protocols is simplified, making it more efficient for organizations to adopt and maintain.
- Centralized authentication streamlines the process of managing user access permissions across different applications and platforms.
Setting Up Server-Based Authentication
Setting up server-based authentication is a crucial step in ensuring the security of your system and protecting sensitive information. Below are the steps to guide you through the process.
Setting up a streaming server can be a daunting task, but with the right guidance, it can be a smooth process. Check out this helpful guide on How to Set Up a Streaming Server to make sure you are on the right track towards seamless streaming experience.
Step 1: Install and Configure Authentication Server
- Choose a reliable authentication server software such as Active Directory, LDAP, or RADIUS.
- Install the chosen software on a dedicated server within your network.
- Configure the server settings according to your organization’s security policies and requirements.
- Set up user accounts and permissions within the authentication server.
Step 2: Integrate Authentication Server with Applications, How to Implement Server-Based Authentication
- Update the settings of your applications to enable server-based authentication.
- Configure the applications to communicate with the authentication server for user verification.
- Implement Single Sign-On (SSO) if needed to streamline the login process for users.
Step 3: Test and Monitor Authentication Process
- Conduct thorough testing to ensure that the server-based authentication is functioning correctly.
- Monitor login attempts and access logs to detect any unusual activity or security breaches.
- Regularly review and update the authentication server configurations to enhance security.
Common Challenges to Avoid
- Avoid using default settings on the authentication server, as they can be easily exploited by attackers.
- Ensure that all network devices and applications are compatible with the chosen authentication server protocol.
- Regularly update the authentication server software to patch any vulnerabilities and ensure optimal security.
Implementing Secure Communication Protocols: How To Implement Server-Based Authentication
When it comes to server-based authentication, implementing secure communication protocols plays a crucial role in ensuring the confidentiality, integrity, and authenticity of data exchanged between the server and clients.
Role of Secure Communication Protocols
Secure communication protocols like SSL/TLS, HTTPS, and SSH are essential in encrypting data transmitted over networks to prevent unauthorized access and interception by malicious third parties.
Ensuring website security is crucial in today’s digital landscape. Explore the latest and most effective digital tools that can safeguard your website from cyber threats. Learn more about the Top Digital Tools for Website Security to keep your online presence safe and secure.
- SSL/TLS: Secure Socket Layer (SSL) and its successor Transport Layer Security (TLS) are commonly used protocols to establish a secure connection between a server and a client. They ensure data confidentiality, integrity, and authentication through encryption.
- HTTPS: Hypertext Transfer Protocol Secure (HTTPS) is a combination of HTTP and SSL/TLS protocols, providing secure communication over the internet. It is widely used for securing sensitive data in online transactions, logins, and other interactions.
- SSH: Secure Shell (SSH) is a cryptographic network protocol used for secure remote access and file transfer over an unsecured network. It provides strong authentication and encryption to protect data from eavesdropping and tampering.
Best Practices for Choosing and Implementing Secure Communication Protocols
When selecting and implementing secure communication protocols, it is essential to consider the following best practices:
- Choose protocols that are widely adopted and proven to be secure by industry standards.
- Ensure proper configuration and maintenance of protocols to mitigate vulnerabilities and security risks.
- Regularly update and patch protocols to address any known security vulnerabilities and weaknesses.
- Implement strong encryption algorithms and key management practices to protect data confidentiality.
- Enforce strict access control measures to authenticate and authorize clients before establishing secure connections.
User Management and Access Control
User management and access control play a crucial role in server-based authentication systems, ensuring that only authorized users have access to resources and sensitive data. Let’s delve into how these aspects are handled in such systems.
User Authentication
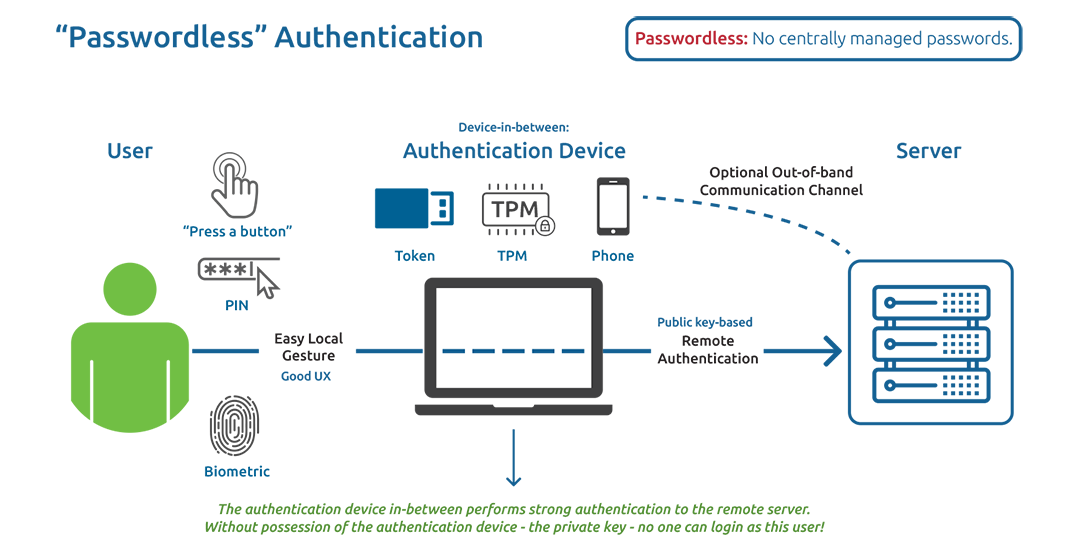
User authentication involves verifying the identity of users trying to access the system. This can be achieved through various methods such as password-based authentication, biometric authentication, two-factor authentication, and more. Tools like OAuth, OpenID, and SAML are commonly used for implementing secure user authentication in server-based systems.
Authorization and Permission Management
Authorization determines what actions users are allowed to perform within the system once they have been authenticated. Permission management involves assigning roles and permissions to users based on their responsibilities and access needs. Frameworks like Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) help in defining and managing user permissions effectively.
Tools and Frameworks for User Management
There are several tools and frameworks available to facilitate user management in server-based authentication systems. Some popular options include Keycloak, Auth0, Okta, and Azure Active Directory. These platforms provide features for user authentication, authorization, and user lifecycle management, making it easier to implement robust user management and access control mechanisms.
Closing Notes
In conclusion, mastering the art of server-based authentication is crucial for safeguarding sensitive information and maintaining a secure digital environment. By following the steps Artikeld in this guide, you can enhance your server security and protect your data effectively. Stay informed, stay secure, and empower your organization with robust authentication practices.