Kicking off with How to Ensure Data Integrity on Your Server, this guide dives into the crucial aspects of maintaining data integrity on your server, offering valuable insights and strategies to safeguard your information effectively.
Importance of Data Integrity
Data integrity is crucial for businesses as it ensures the accuracy, consistency, and reliability of the information stored on a server. When data integrity is compromised, it can lead to serious consequences that can impact operations and decision-making processes.
Enhance your brand strategy with the help of digital tools that can elevate your online presence. Learn how to utilize the latest technologies and strategies outlined in How to Use Digital Tools to Enhance Your Brand Strategy to create a strong and memorable brand identity.
Empower your brand with the tools needed to succeed in the digital landscape.
Significance of Data Integrity
Maintaining data integrity is essential for businesses to make informed decisions based on accurate and reliable information. Without data integrity, organizations risk making faulty decisions that can lead to financial losses, damage to reputation, and legal implications.
Potential Risks of Compromised Data Integrity
Compromised data integrity can result in various risks such as:
- Data loss: Inaccurate or incomplete data can lead to loss of critical information needed for business operations.
- Data breaches: When data integrity is compromised, it opens up opportunities for hackers to gain unauthorized access to sensitive information.
- Compliance issues: Failure to maintain data integrity can result in non-compliance with data protection regulations, leading to penalties and legal consequences.
Impact of Data Integrity Issues on Businesses
Data integrity issues can have detrimental effects on businesses, including:
- Inaccurate reporting: Without data integrity, reports generated for decision-making purposes may be unreliable and inaccurate.
- Loss of customer trust: Data integrity issues can erode customer trust and confidence in the organization’s ability to protect their information.
- Operational disruptions: Compromised data integrity can disrupt business operations, leading to inefficiencies and delays in service delivery.
Implementing Data Backups
Regular data backups are crucial for maintaining data integrity on your server. Backing up data ensures that in case of any unexpected events such as hardware failures, cyber attacks, or accidental deletions, you can restore your data and continue operations smoothly.
Importance of Regular Data Backups
- Performing regular backups helps protect your data from loss or corruption.
- It provides a safety net in case of emergencies, ensuring business continuity.
- Backups can also help in complying with data protection regulations and industry standards.
Different Methods for Creating and Storing Backups Securely, How to Ensure Data Integrity on Your Server
- Utilize cloud storage services to store backups offsite for added security.
- Use external hard drives or network-attached storage (NAS) devices for local backups.
- Implement disk imaging software to create exact copies of your server’s data for comprehensive backups.
Frequency of Backups
Perform backups regularly based on the volume of data changes on your server. It is recommended to:
- Perform daily backups for critical data that changes frequently.
- Weekly backups for less critical data that doesn’t change as often.
- Monthly backups for archival purposes or historical data that remains static.
Access Control and User Permissions
Access control plays a crucial role in ensuring data integrity on your server. By managing who has access to sensitive information, you can prevent unauthorized alterations or deletions that could compromise the integrity of your data.
Best Practices for Setting User Permissions
- Use the principle of least privilege, granting users only the permissions they need to perform their tasks. This reduces the risk of accidental or intentional data manipulation.
- Regularly review and update user permissions to ensure they align with current roles and responsibilities within your organization.
- Implement role-based access control (RBAC) to streamline the process of assigning permissions based on job functions or responsibilities.
- Utilize strong authentication methods, such as multi-factor authentication, to verify the identity of users before granting access to sensitive data.
Strategies for Limiting Access to Sensitive Data
- Encrypt sensitive data to protect it from unauthorized access, even if a breach occurs.
- Implement access control lists (ACLs) to specify which users or groups can access specific files or directories.
- Regularly audit user activity logs to detect any unauthorized access attempts or suspicious behavior.
- Train employees on the importance of data security and the proper handling of sensitive information to minimize the risk of data breaches.
Data Encryption Techniques
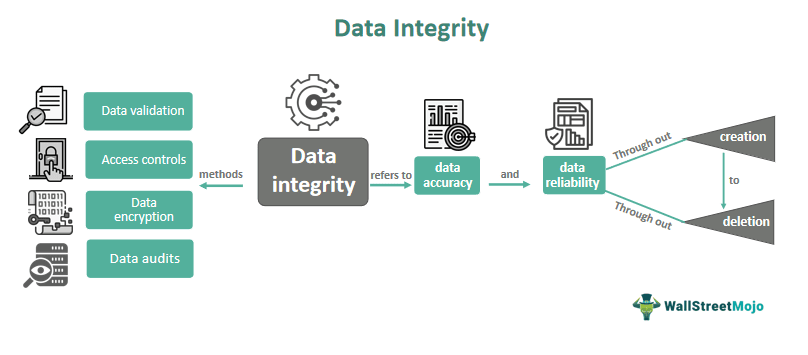
Data encryption is a crucial method to protect the integrity of data on a server. By converting plain text into ciphertext using encryption algorithms, sensitive information is safeguarded from unauthorized access.
Revolutionize your email marketing campaigns with the power of digital tools that can streamline your efforts and boost your results. Discover how the How Digital Tools Can Improve Your Email Marketing Campaigns to engage your audience effectively and drive conversions.
Elevate your email marketing game with the right tools at your disposal.
Symmetric Encryption
Symmetric encryption uses a single key to both encrypt and decrypt data. Common algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). While symmetric encryption is efficient for securing data at rest, the challenge lies in securely sharing the key between parties.
Embrace the power of digital tools for content repurposing to breathe new life into your existing materials. By utilizing the Top Digital Tools for Content Repurposing , you can reach a wider audience and maximize the impact of your message.
Stay ahead of the game by exploring innovative ways to refresh and repurpose your content.
Asymmetric Encryption
Asymmetric encryption involves a pair of keyspublic and private. The public key is used to encrypt data, while the private key is required for decryption. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are popular asymmetric encryption algorithms. This method is ideal for secure data transmission as the public key can be shared without compromising data security.
Hashing Algorithms
Hashing algorithms like SHA-256 (Secure Hash Algorithm) are used to create unique fixed-length hash values from input data. While hashing is not technically encryption, it is essential for verifying data integrity. By comparing hash values, any alterations to the original data can be detected.
Importance of Data Encryption
Encrypting data is essential both in transit and at rest to ensure confidentiality and integrity. Data encryption protects sensitive information from unauthorized access, reducing the risk of data breaches and maintaining compliance with data protection regulations.
Monitoring and Auditing: How To Ensure Data Integrity On Your Server
Monitoring and auditing are crucial aspects of ensuring data integrity on a server. By keeping track of data access and changes, you can identify any unauthorized activities and maintain the accuracy and reliability of your data.
Importance of Monitoring Data Access and Changes
Monitoring data access and changes helps in detecting any unusual behavior or unauthorized access to sensitive information. It allows you to track who accessed the data, when it was accessed, and what changes were made, enabling you to take immediate action if any anomalies are detected.
Tools and Techniques for Auditing Data Integrity
- Use logging tools: Implement logging mechanisms to record all data access and changes, including user activities and system events.
- Regular audits: Conduct regular audits to verify the integrity of data on your server and ensure compliance with security policies.
- Automated monitoring systems: Utilize automated monitoring systems to continuously track data access and changes in real-time.
Best Practices for Detecting and Responding to Data Integrity Breaches
- Establish access controls: Limit access to sensitive data to authorized personnel only and implement user permissions to control who can view, modify, or delete data.
- Encryption: Use data encryption techniques to protect data at rest and in transit, ensuring that even if data is compromised, it remains unreadable to unauthorized users.
- Regular backups: Maintain regular backups of your data to restore information in case of a data integrity breach or loss.
- Incident response plan: Develop an incident response plan outlining steps to be taken in case of a data breach, including investigation, containment, eradication, and recovery.
Closure
In conclusion, ensuring data integrity on your server is paramount for the security and reliability of your data. By implementing the Artikeld practices, you can fortify your defenses and minimize the risks of data breaches. Stay vigilant and proactive in maintaining data integrity to safeguard your valuable information.